Create Google SecOps integration
Introduction
The Stairwell Enrichment Integration for Google SecOps provides automated, in-line enrichment of indicators of compromise (IOCs) such as hashes, IP addresses, and hostnames.
By connecting SecOps cases directly with Stairwell’s malware corpus and organizational vault, analysts gain immediate context about suspicious artifacts.
This reduces the need for manual pivots, accelerates investigations, and provides richer insights within the case workflow itself.
Enrichment Flow
Extraction: SecOps extracts the IOC from the case
- Forwarding: The IOC is sent to Stairwell.
- Matching: Stairwell checks the IOC against its malware corpus or the organization’s private vault.
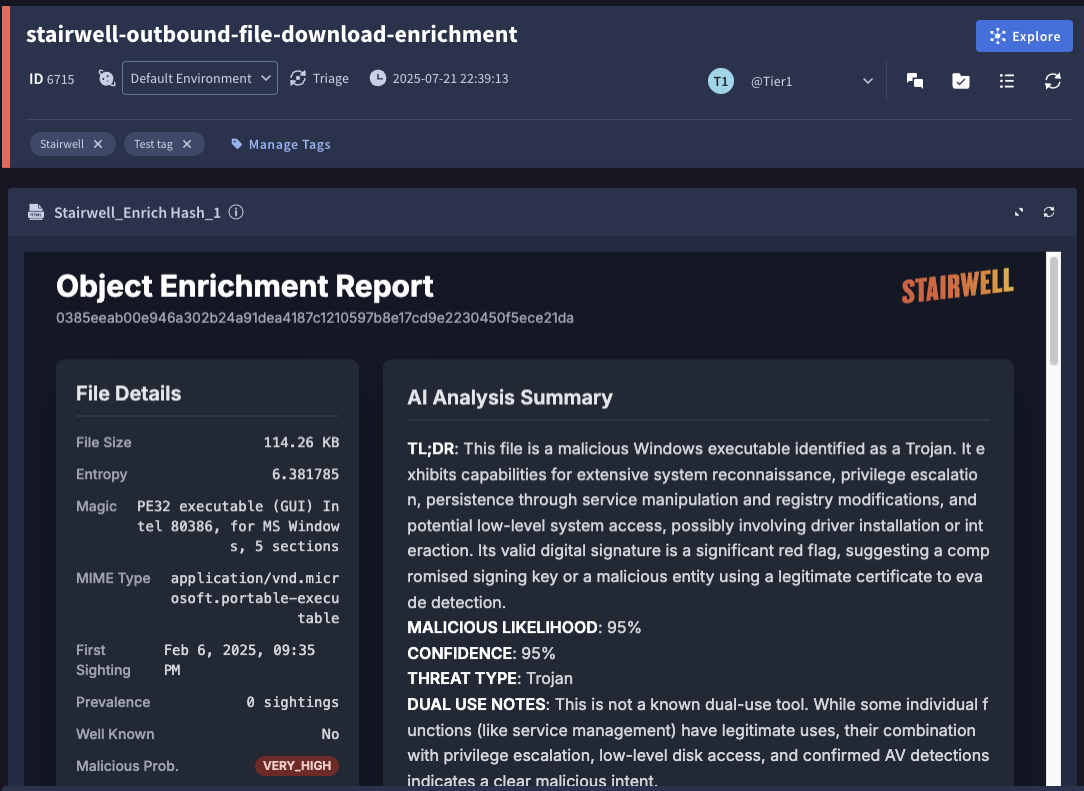
- Response: Stairwell returns structured, rich data including verdicts, YARA rule matches, prevalence, variants, registry keys, embedded files, persistence mechanisms, AI-driven summaries, unpacked payloads, dropped files, and anti-analysis details.
Analyst Experience
- Enrichment results appear directly in the case timeline.
- No need to pivot into other tools or detonate files.
- Analysts can immediately understand what the file or IOC does and how it relates to others.
How to Connect Stairwell to Google SecOps
Installation
- Go to Marketplace → Response Integrations
- Search for Stairwell
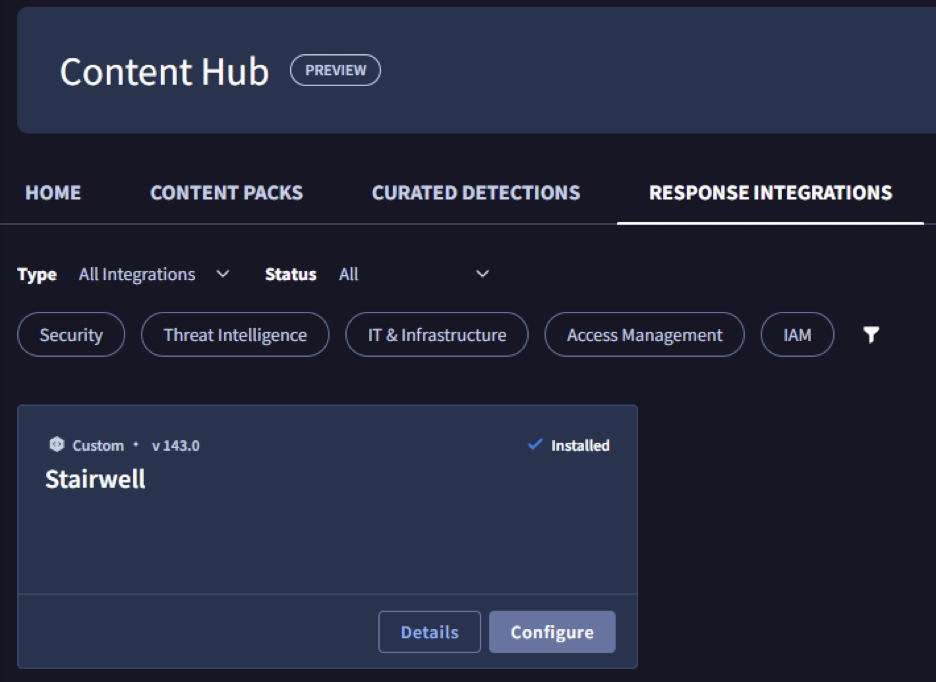
- Click Install
Configuration
- Navigate to Response → Integrations Setup
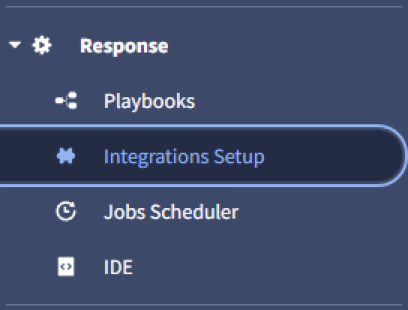
- Click Create a new instance and choose Stairwell
- Enter the parameters:
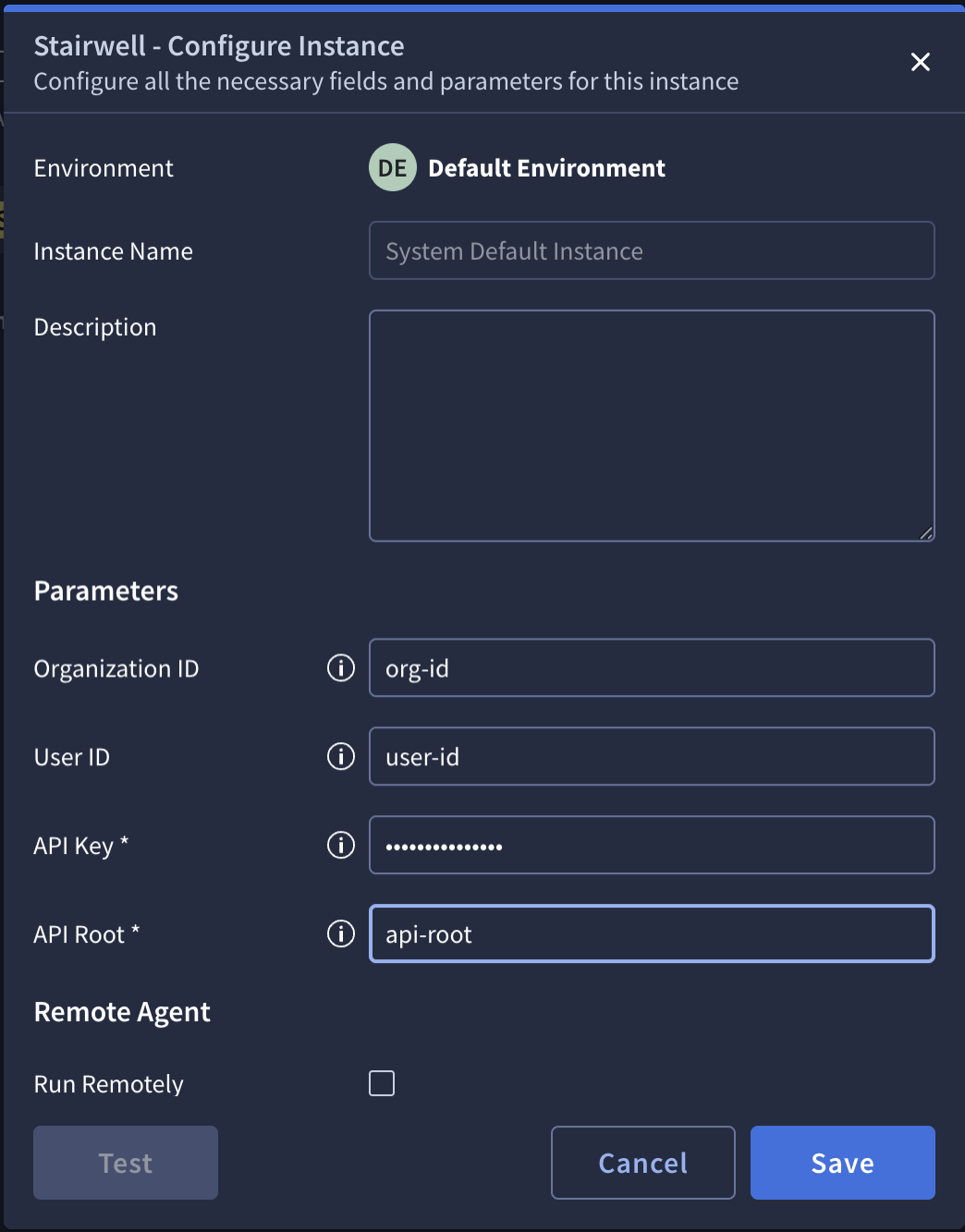
Parameters:
- Organization ID
- User ID
- API Key
- API Root
- Save and click Test to verify connectivity.
Case View Setup
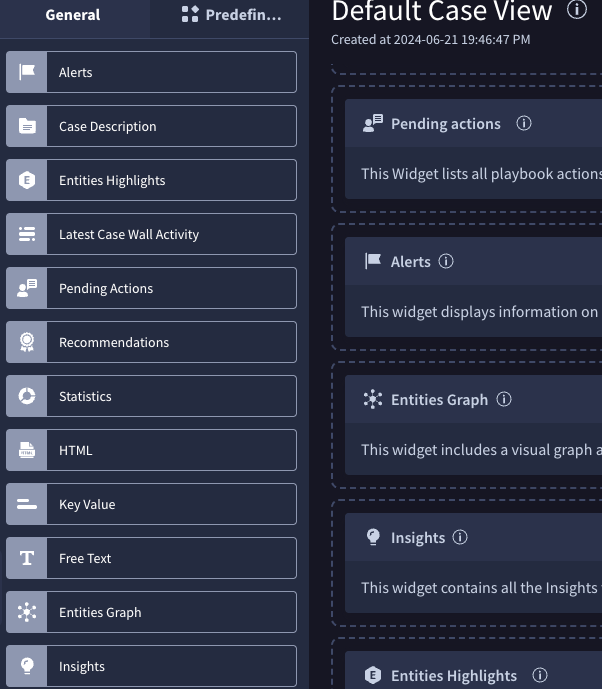
- Navigate to Settings → SOAR Settings → Case Data → Views
- Select Default Case View
- Add the Insights widget under General to enable IOC enrichment visibility inside cases.
Usage in Playbooks
- Search for Stairwell in the playbook step selection panel.
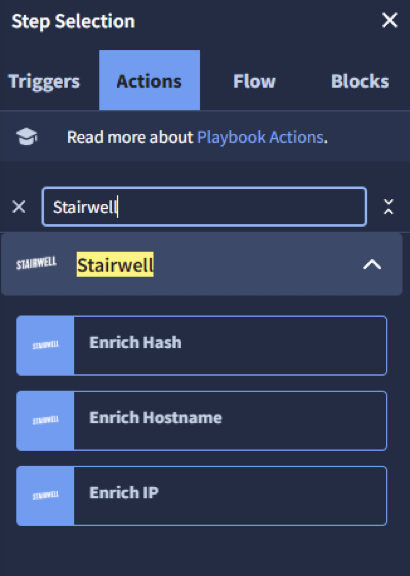
- Actions are prebuilt with widgets for enrichment results.
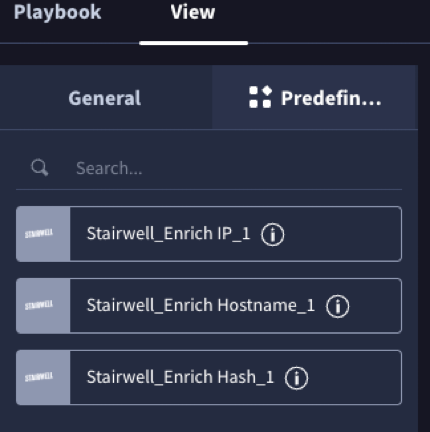
Supported enrichment actions:
- Enrich Hash – Returns file metadata, verdicts, YARA matches, signatures, and AI summaries.
- Enrich Hostname – Returns DNS records, verdicts, and comments.
- Enrich IP – Returns verdicts, opinions, and sightings.
Enrichment actions are trigger-agnostic: Whether cases are created from EDR alerts, SIEM correlations, or other playbooks — if they include a hash, IP, or hostname, Stairwell can enrich them.
Troubleshooting
- Go to the IDE under Response.
- Select the action within Exchange, click Play Item, and review the Debug Output for detailed response information.
Updated 4 months ago
