Step 4: Explore
Once deployment has begun, it's important to begin to explore the Stairwell platform. Stairwell can enable and empower teams discovery vulnerable files, uncovered unapproved software, analyze malware, scope investigations and impact, and so much more. It's important to log into Stairwell early and often so that you can get familiar with all the uses that span across security operations, threat hunting, and incident response.
- Search
This default home screen allows you to conduct various searches. Beginners can take advantage of our natural language search feature, which turns everyday language into effective, focused searches. We also have a query builder designed to help users get acquainted with the data model and the platform's search capabilities. Moreover, we provide pre-configured searches that quickly pinpoint intriguing objects. For advanced users, we offer the sophisticated CEL search option.
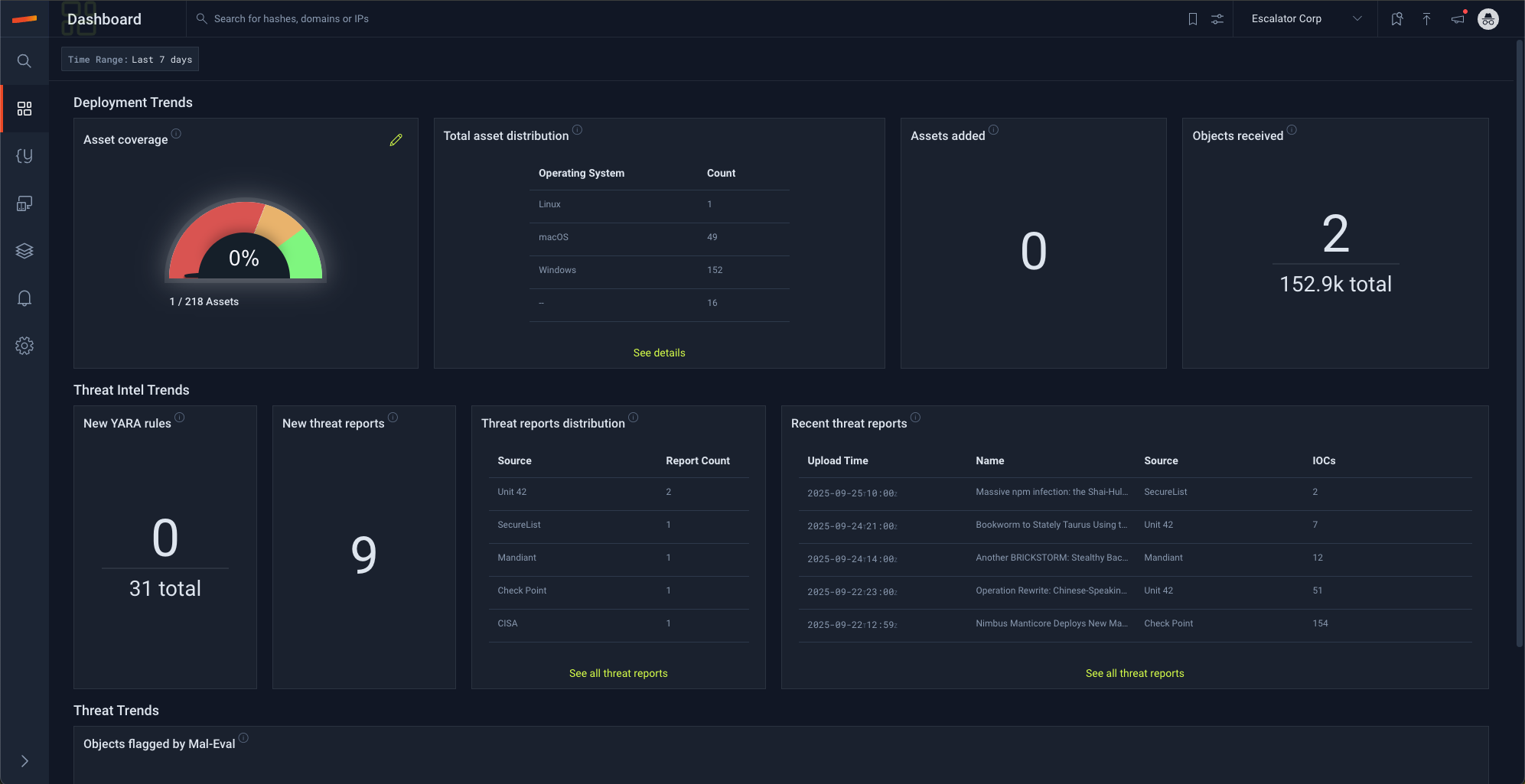
- Dashboard
The dashboard is a quick stop to review health and state of assets, objects, rules, reports, and more.
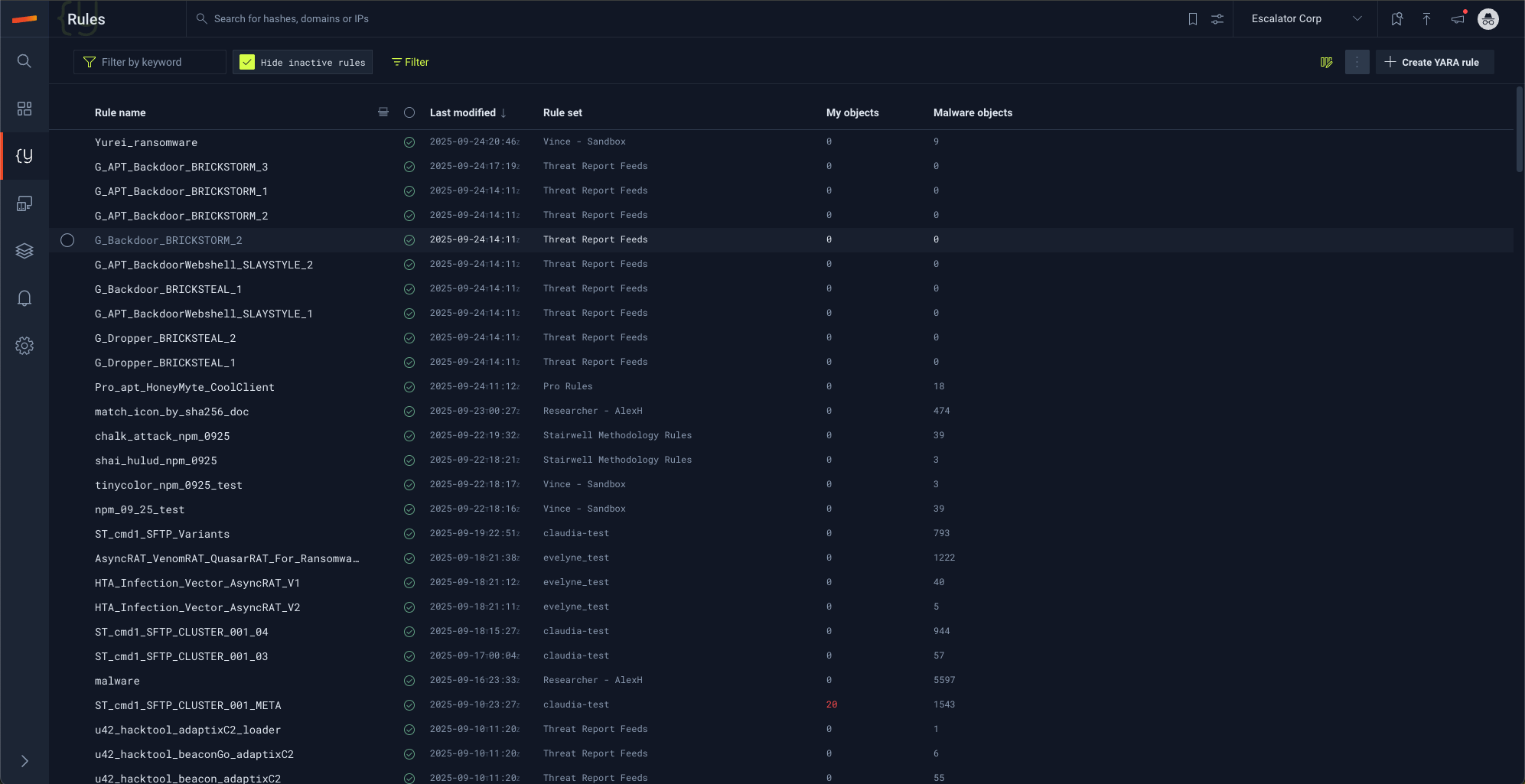
- YARA Rules
The YARA rules section is a powerful section that allows users to review, create, modify, and delete rules. From here users can also click into rules and results to pivot into interesting matches.
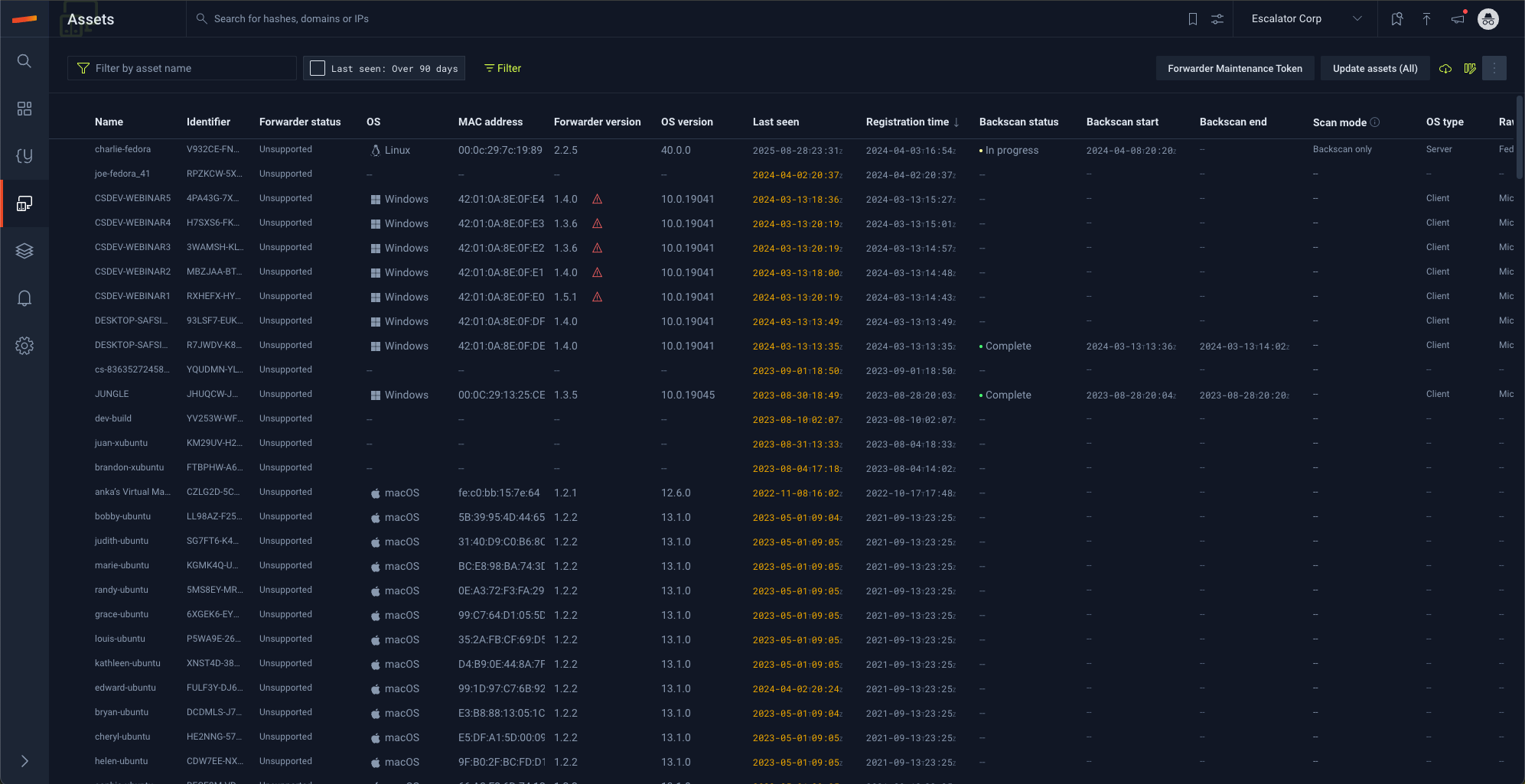
- Assets
The assets screen is designed to display the status and condition of assets. It not only provides details about the assets, including names, identifiers, operating systems, and more, but also offers insights into the scanning and uploading status of the forwarder. From this screen, users can upgrade forwarder versions, organize assets into groups, implement and tailor forwarder policies, establish exclusions and filters, and ultimately, delve into notable objects observed on the assets.
- Threat Reports
In the threat reports section of the Stairwell UI, you'll see all the threat reports that Stairwell or your team has identified, uploaded, parsed, and ran against your data. This is a quick and easy way to see if any published indicators of compromise are seen in your environment(s), and if so, where and when.

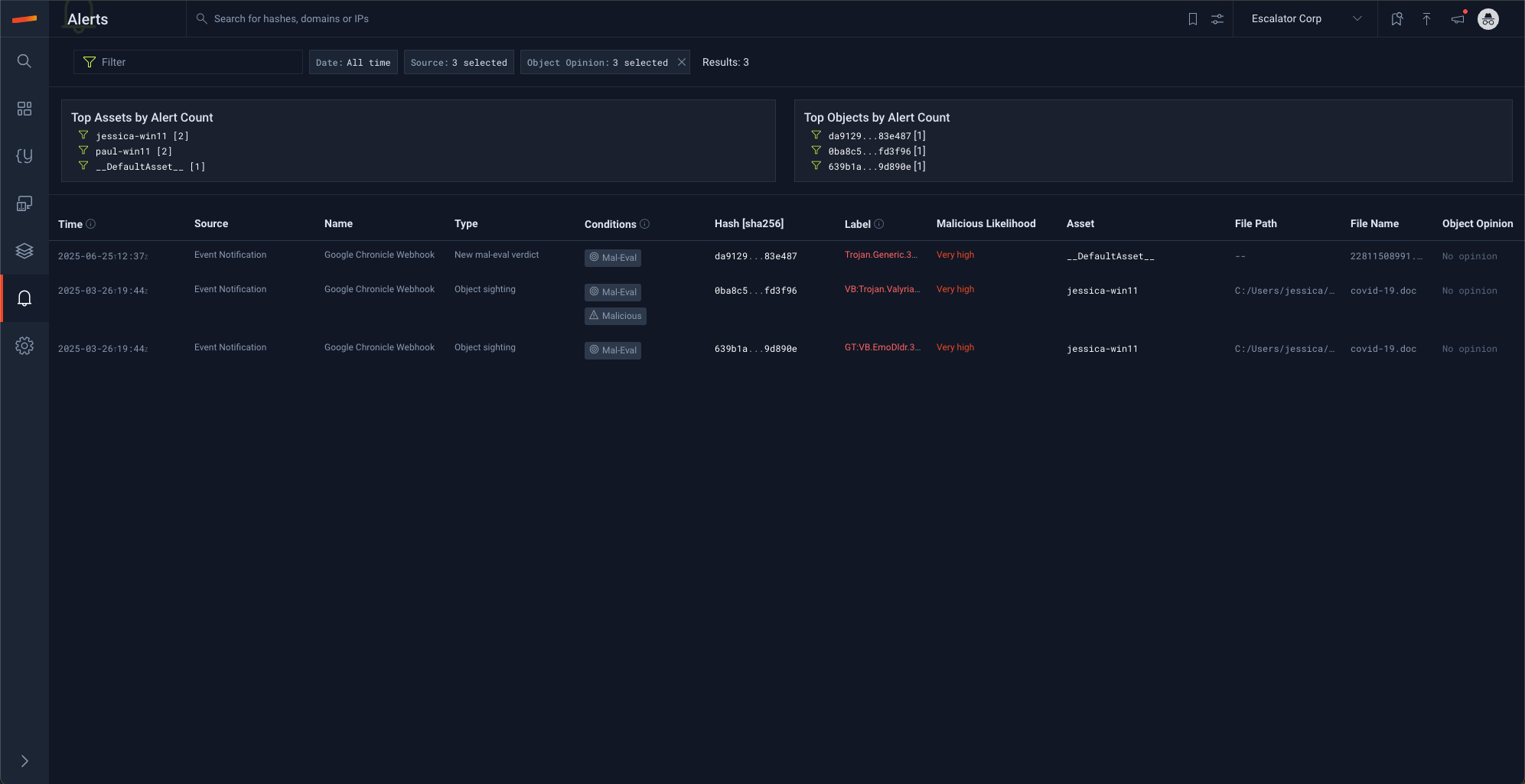
- Alerts
In the alerts section of the Stairwell UI, you'll be able to see the items configured as conditions in event notifications as well as some of the items Stairwell marks for escalation through MalEval.
- Settings
In the setting section of the Stairwell UI, you'll be able to view and modify several preferences and configurations.
Account: this section will allow you to see your details along with modifying several aspects like timezone preference, default environment, and more. These settings are specific to your account and do not transfer to other users in your organization.
Environments: this section will allow you to manage settings that apply to environments including policies, groups, registrations, exclusions and intake filters.
Organization: this section will allow you to see manage properties that apply across the entire organization including environments your organization has access to, users, SSO and auth tokens.
Integrations: this section will allow you to setup your own alerting conditions and destinations to operationalize the data from Stairwell with the rest of your security technology.
Updated 5 months ago
