How to Perform a Bulk Search with Unstructured Data
Introduction
Security data is often messy and embedded within unstructured text like threat reports, blog posts, or ISAC alerts. Manually extracting, defanging, and searching each Indicator of Compromise (IoC) is time-consuming and prone to error.
Stairwell's search bar simplifies this entire process. You can paste large volumes of unstructured text (even an entire web page) directly into the search bar, and the platform will automatically parse, identify, and search for all relevant indicators within your environment.
How to Use Bulk Search
Follow these steps to search using unstructured data:
- Find Your Source: Navigate to your source of intelligence. This can be a threat report, an email alert, or any page containing data you want to search for.
- Copy the Content: Select and copy all the text from the source. A common shortcut is to press
Ctrl + A(Select All) and thenCtrl + C(Copy). - Paste and Search: Paste the entire block of copied text directly into the main Stairwell search bar and press Enter.
How It Works
When you paste the text, Stairwell automatically performs the following actions:
- Parses: Scans the entire text for known indicator types.
- Extracts: Identifies all relevant IoCs, such as file hashes (SHA256, MD5, SHA1), domains, IP addresses, and other attributes.
- Defangs: Automatically handles "defanged" indicators (e.g.,
hxxp://orexample[.]com) so you don't have to clean them up. - Searches: Instantly runs a search across your entire environment for every indicator found.
Example Workflow: Akira Ransomware Report
Let's use the Decrypted: Akira Ransomware report from Avast as an example.
Instead of manually reading the 7-minute report and copying individual IoCs, we can simply:
- Go to the URL.
- Press
Ctrl + Ato select the entire page. - Paste the contents into the Stairwell search bar.
The platform immediately parses all indicators from the report and returns any matches, providing instant results without any manual data cleanup.
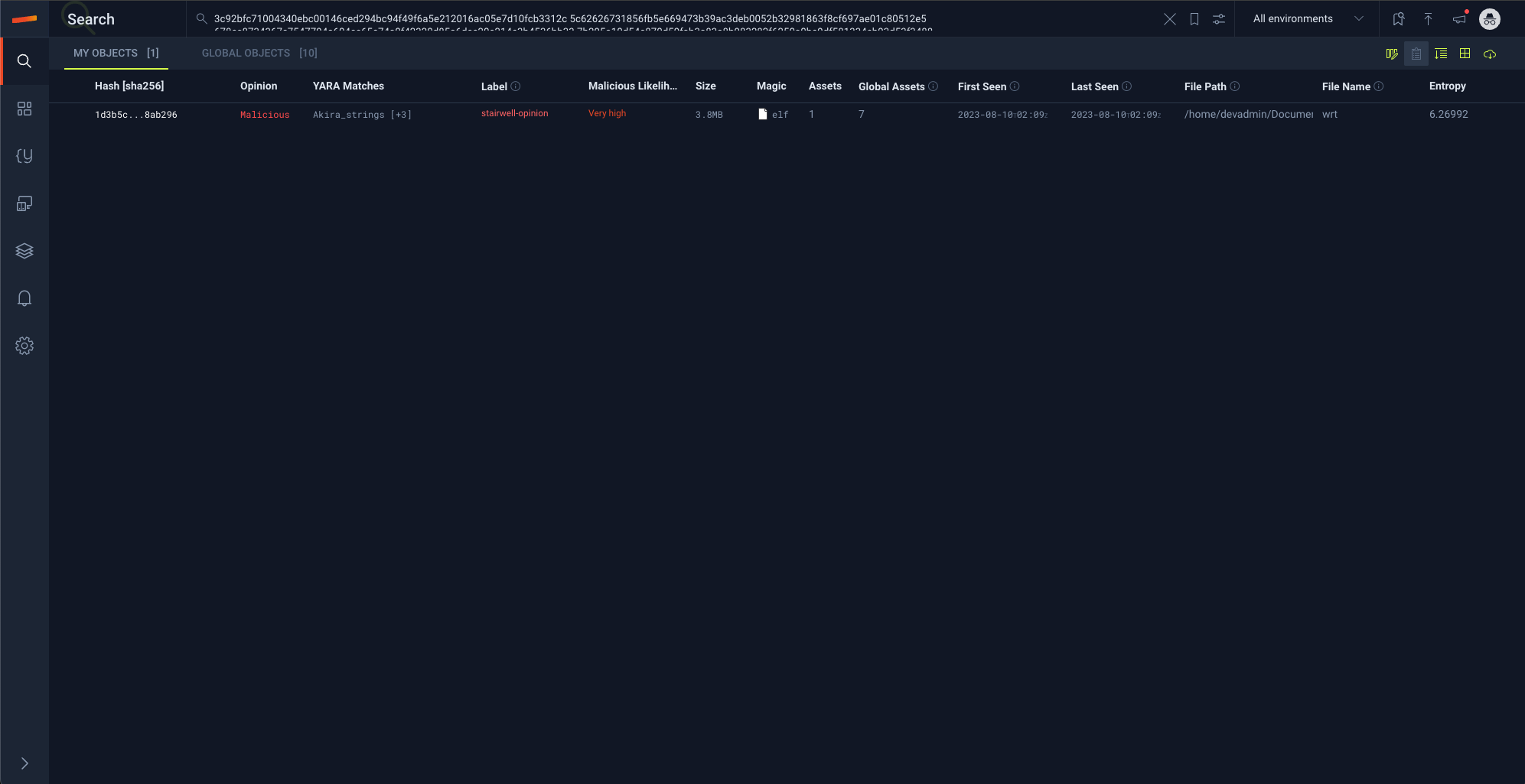
This "copy-paste" workflow drastically reduces the time from initial intelligence to actionable results.
What's Next?
After your bulk search returns results, you can:
- Click on any matched object to begin your investigation.
- Select a high-priority file Run AI Triage and use Run to Ground (RTG) to see its full history.
Updated 4 months ago
