What is a Threat Report?
Threat Reports in the Stairwell platform are where public and private threat intelligence reports are operationalized across all objects in a customer environment. There are countless research teams around the globe that produce analysis reports of cyber threats. These reports typically focus on a specific threat actor group/campaign, a novel new attack technique, or the exploitation of a previously unknown vulnerability. As such, these reports often contain indicators of compromise (IoCs) that have a specific association to the subject matter of the report like file hashes, network indicators, or specific file attributes like strings.
Historically, cyber-threat intelligence operators consumed these reports manually and extracted the IoCs by copying and pasting or imported them into a Threat Intelligence platform (TIP). Stairwell, having been built by practitioners that did this very thing day in and day out for years, automated not only the consumption of threat intelligence (TI) reports but also the operationalization of the resulting indicators.
In the Stairwell platform, navigate to the Threat Reports page and as the page loads you will see something interesting happen:
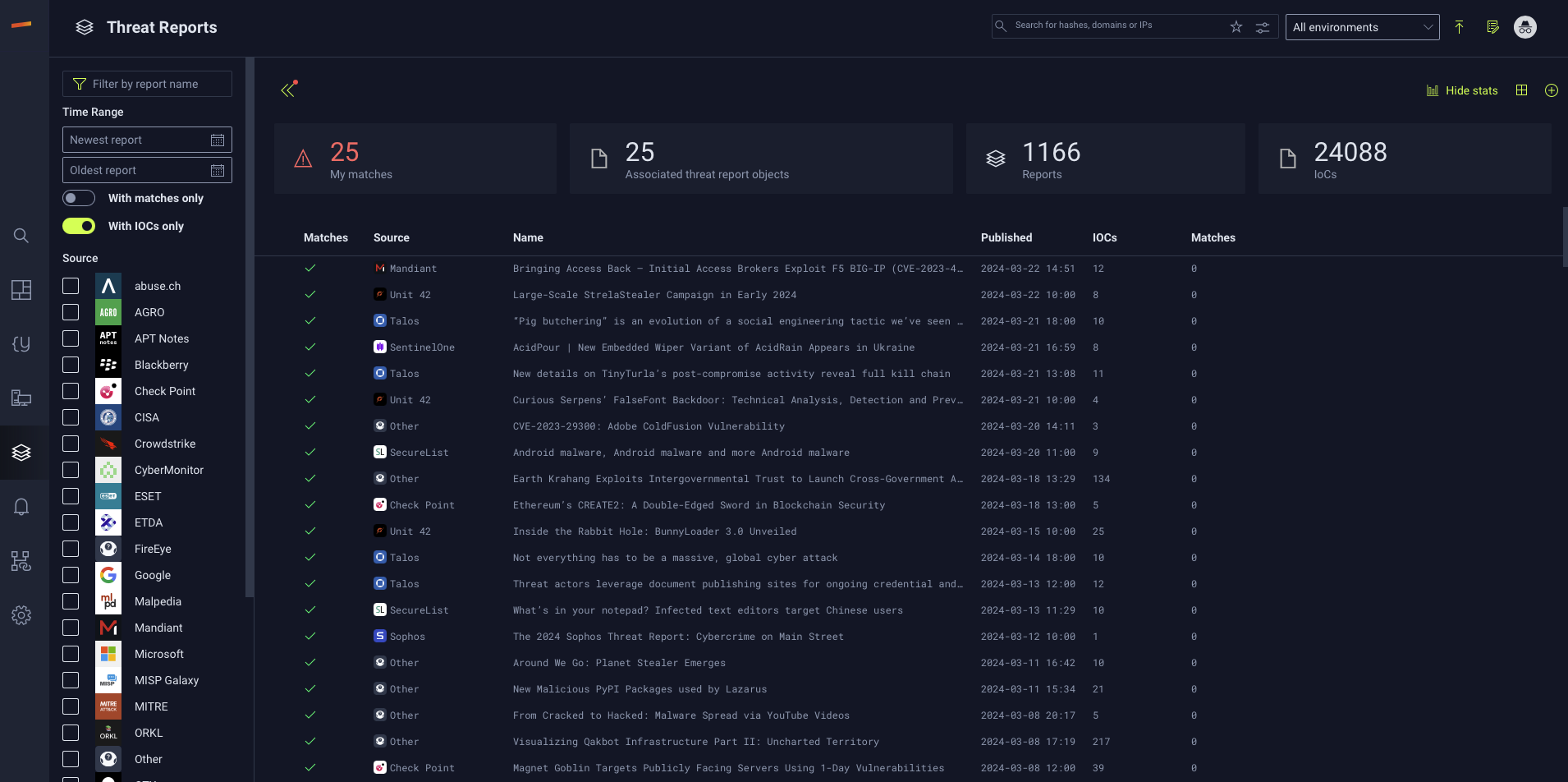
Every time the page loads, the empty squares under "Matches" beside each report render to show a green checkmark (no matches) or a red triangle with an exclamation point (matches found). See the example below to witness the differences.
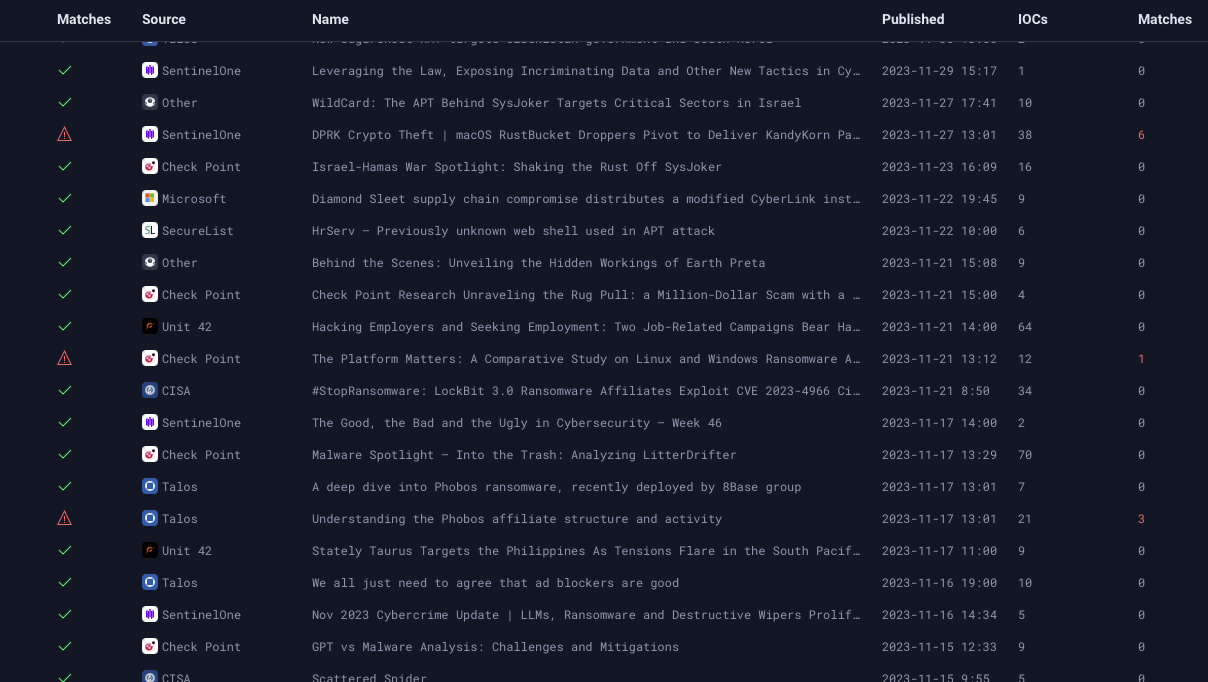
Every time the threat report page loads, every IoC from every threat report is checked across every file in your environment.
Threat reports are snapshots of the greater picture of a malware attack. Once the report is published, those indicators are typically known to the world within minutes which means threat actors need to immediately change their payloads if they have any hope of bypassing signature based detection. This means variants of threats found in that report start to emerge and Stairwell's variant discovery makes matches to IoCs in those reports too. As new files appear on your assets over time and as new variants emerge, Stairwell 's detection stays on at all times looking for threats.
Every new threat report gets ingested, automatically parsed, and checked against every file in your environment in less than 5 minutes after it gets published. When someone from executive leadership wants to know if you've been affected by a new threat they just heard about from an authoritative source, you now have an answer.
What threat report sources are covered?
When you click the filter icon on the threat reports page, a side menu appears showing you all the current feeds automatically ingested. There is also where you will find a toggle switch to only show threat reports that have matches to your environment
"Filter by object matches".
What about feeds from an independent researcher you follow or a trust group you or your organization is a member of?
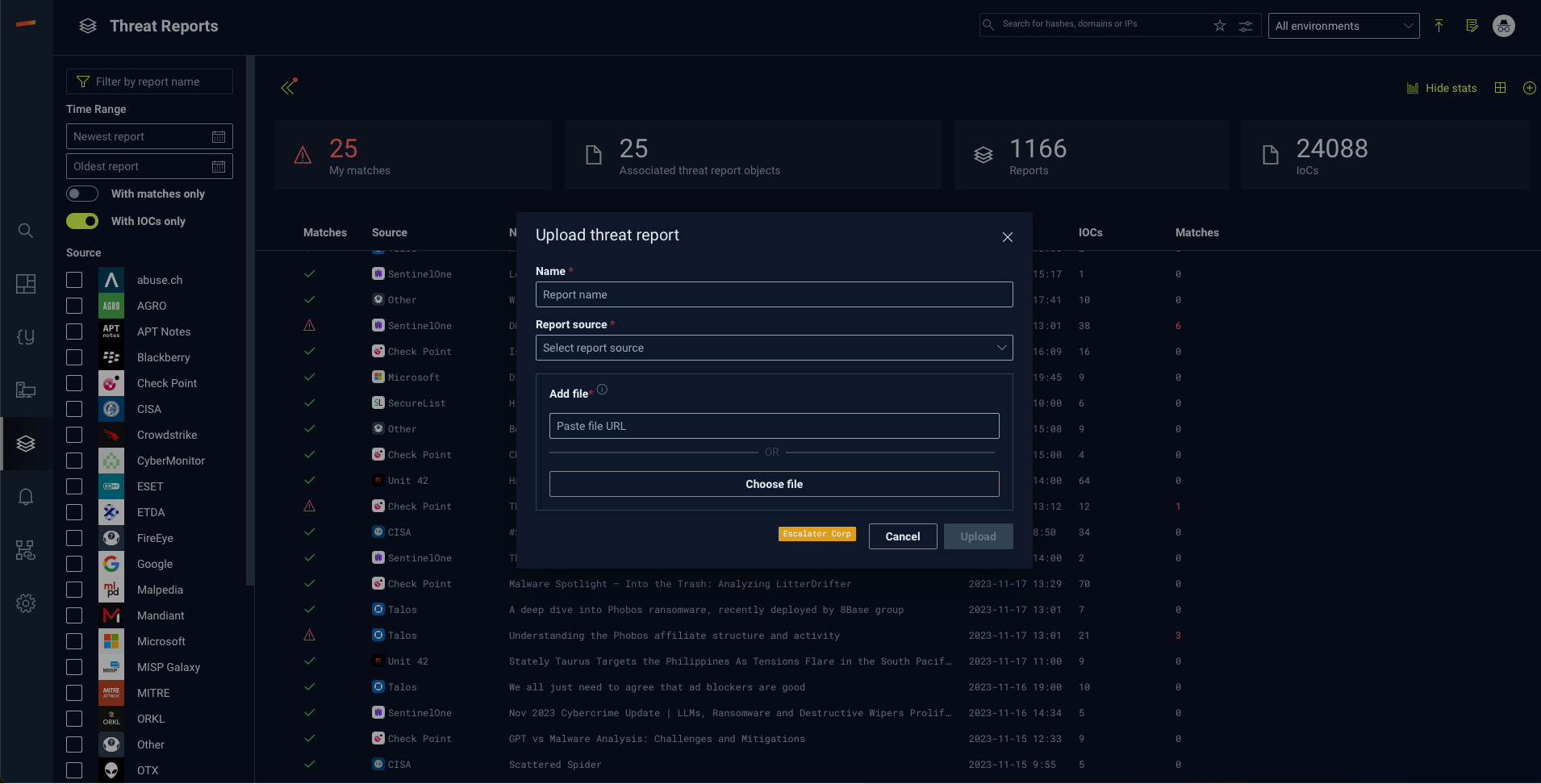
You can add or upload reports to your environment by clicking the plus (+) button at the top right corner of the Threat Reports page and supply a URL or upload a txt, json, or stix file privately to only your environment. The Stairwell platform will parse the file and add it to your threat reports but note that it will not be shared with any other environments.
Alternatively, if you come across a report you only want to search for in the platform, you can simply copy all the text from the report and paste it into the search bar and we will extract all the IoCs out for you
Updated 5 months ago
