Release Notes (2023-03)
March release notes detailing the evolution of the Stairwell platform
March 30th, 2023
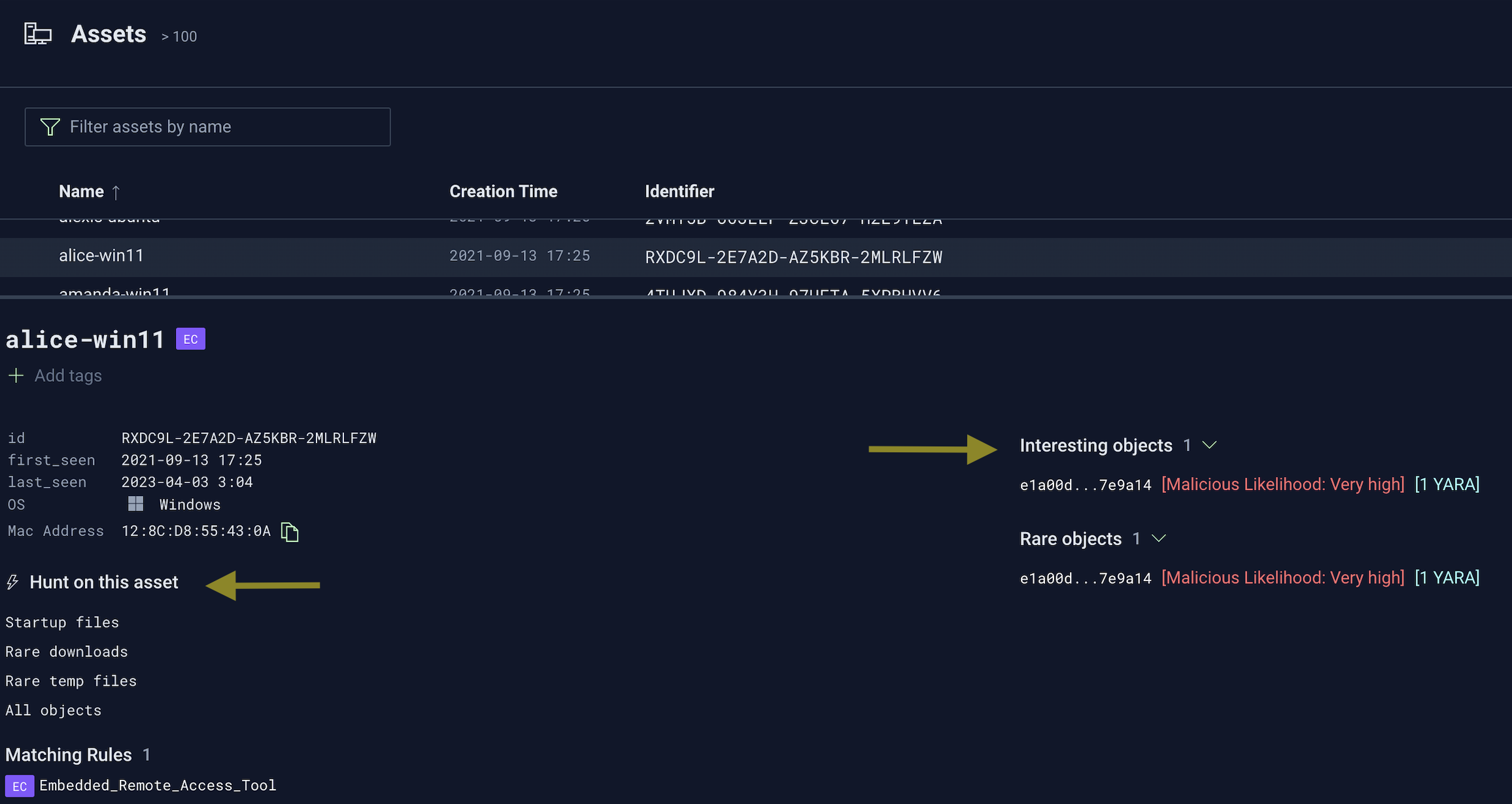
Enhancement: Improved asset details page
The details associated with a given asset have been restructured to help you:
Quickly view suspicious/rare files on a per-asset basis
Pivot and perform asset-specific hunts
The following screenshot highlights the new sections that are included in asset details:
Hunt on this asset is a collection of pre-built search queries that you can leverage to quickly pivot towards interesting artifacts, like rare downloads, temp files, etc.
Interesting objects are surfaced files that are deemed suspicious and/or rare for the particular asset.
March 21st, 2023
New Feature: Threat Reports! 🎉
We're thrilled to announce Inception's latest major feature: Threat Reports!
Threat Reports is an automatic consumption of leading threat intelligence from sources like Unit42, Mandiant, CrowdStrike, etc., where IOCs and YARA rules are automatically parsed and searched against your private files.
You can click into the new Threat Reports interface from the primary navigation menu (see below) to quickly glean the reports that have been most recently ingested:
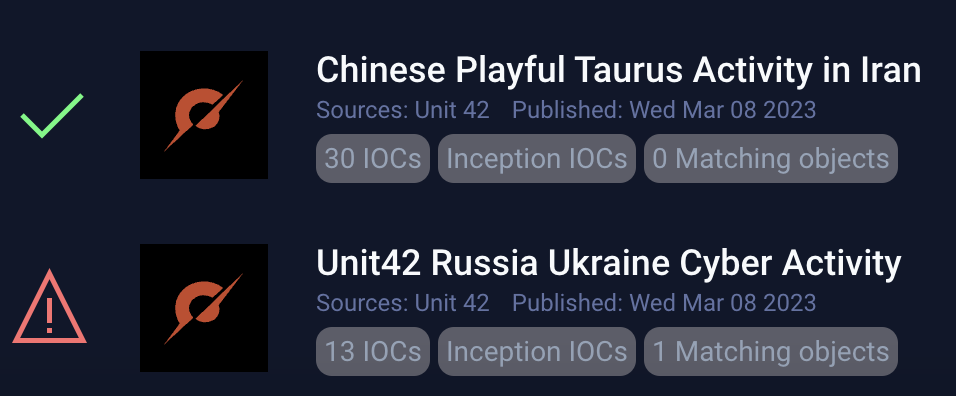
Each report will indicate the following:
- Am I impacted?
- How many IOCs were parsed
- How many matching objects were found
The green check box (✅) is a visual indicator that no matching intelligence was found within your organization - no impact!
Conversely, a red caution icon indicates that Inception identified files within your organization that have IOC matches:
You can click into any report to view additional information:
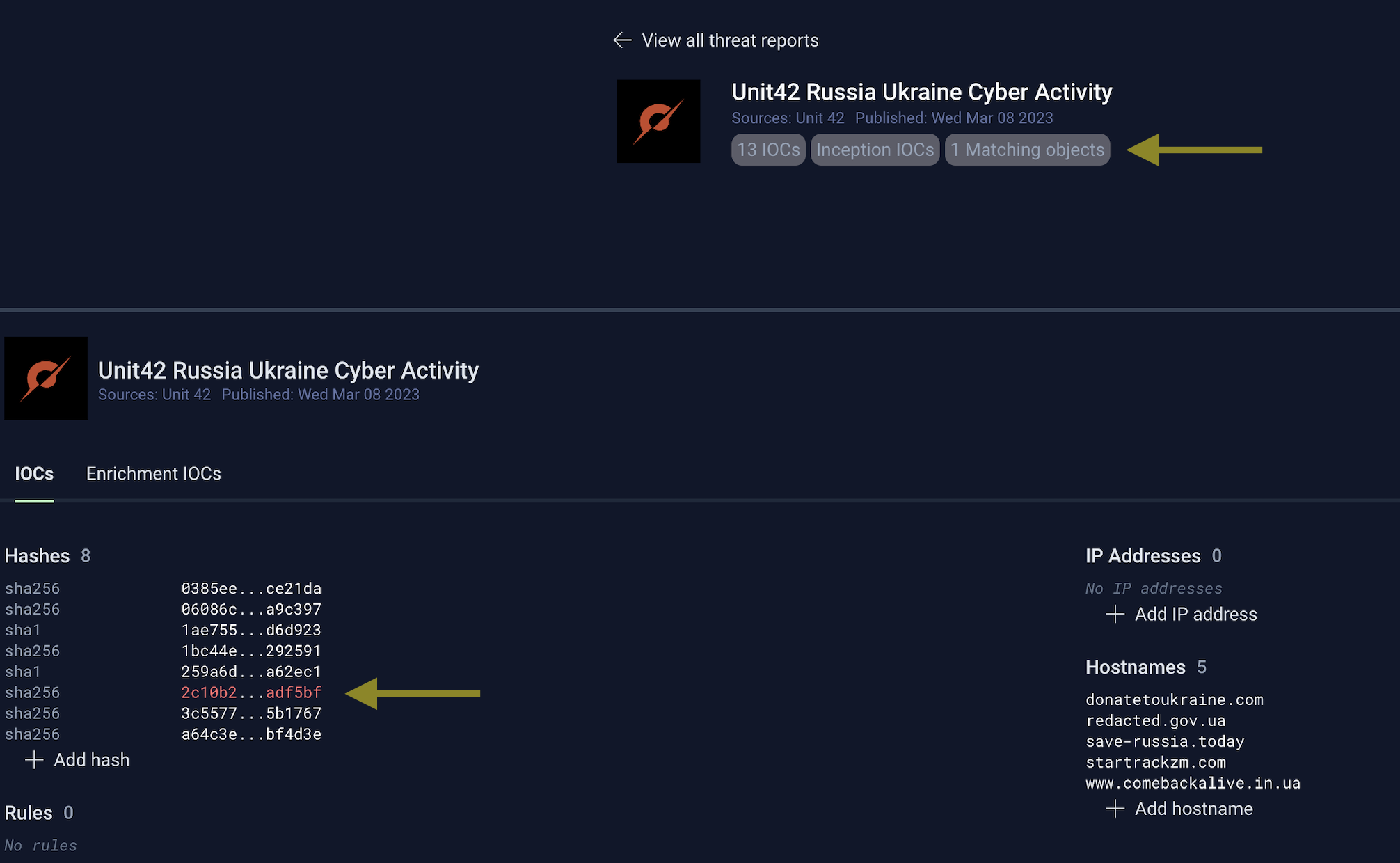
The detailed report view (shown above) will list all of the IOCs that were parsed and searched against:
- Hashes
- IP addresses
- Hostnames
- YARA rules
Any indicator listed in red indicates a positive match in your environment. For example, the red SHA-256 hash (in the screenshot above) denotes that particular hash has been seen within your private instance.
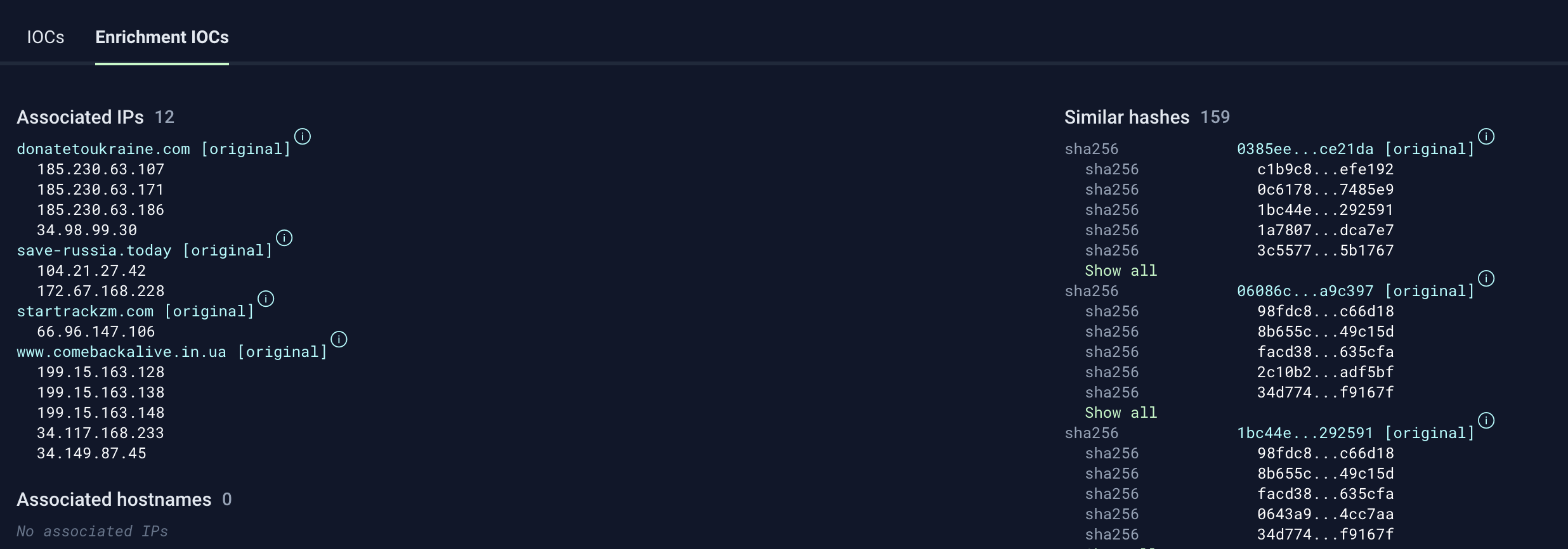
Inception automatically enriches IOCs in a number of ways, to include leveraging historical active DNS data to show additional correlations between IP addresses and hostnames, in addition to automatically running variant searches against hashes/files that were extracted from threat reports:
March 20th, 2023
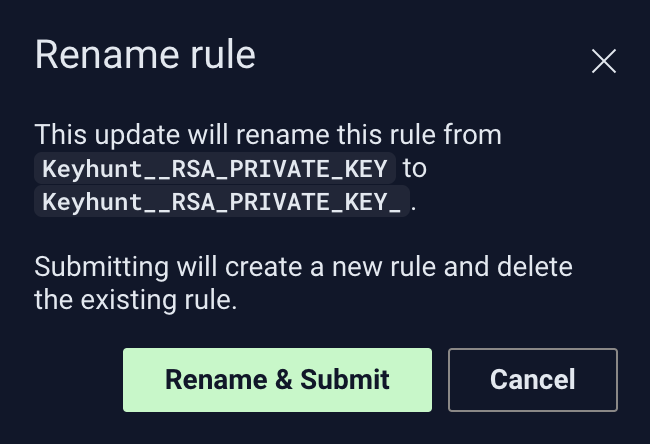
Quality of Life Improvement: You can now re-name YARA rules ✨
You can now rename your YARA rules post-creation. Simply click the "edit" button within the YARA rules page and re-name your rule within the editor.
You will be prompted to verify the new rule name:
March 16th, 2023
Enhancement: Additional asset metadata collected and presented
The asset management page now includes additional metadata about machines that are running the Windows file forwarder:
- Backscan start time
- Backscan end time
- OS type
- Raw OS
March 14th, 2023
Enhancement: Last Seen Times
Last Seen times have been infused into the product, affording the ability to quickly glean the most recent time an object was seen in association with a particular asset and/or location ("First Seen" times were already present).
You will see Last Seen times in two key areas:
-
Object list page
-
Object details pane
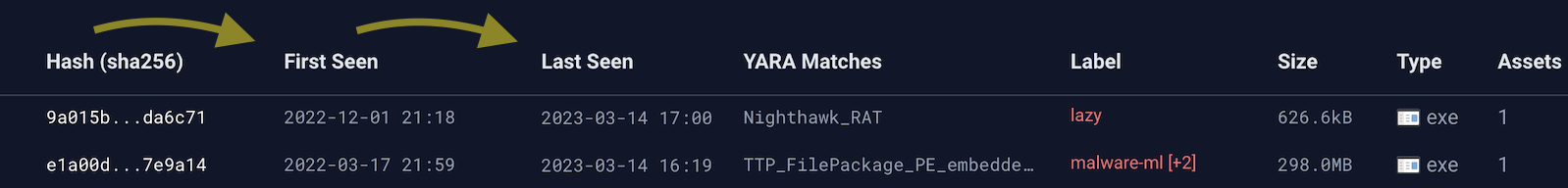
The Last Seen times are calculated by when the Inception file forwarder reports file-related activity on a previously collected file. For example, Inception will tell you the first time it ever observed an artifact, in addition to the most recent time it was observed subsequently to being originally collected.
March 13th, 2023
New Feature: New Alerts page! 🎉
The new "Alerts" page is a one-stop-shop for identifying and triaging files that Inception deems malicious with high confidence.
There is a new dedicated top-level navigation option for Alerts:
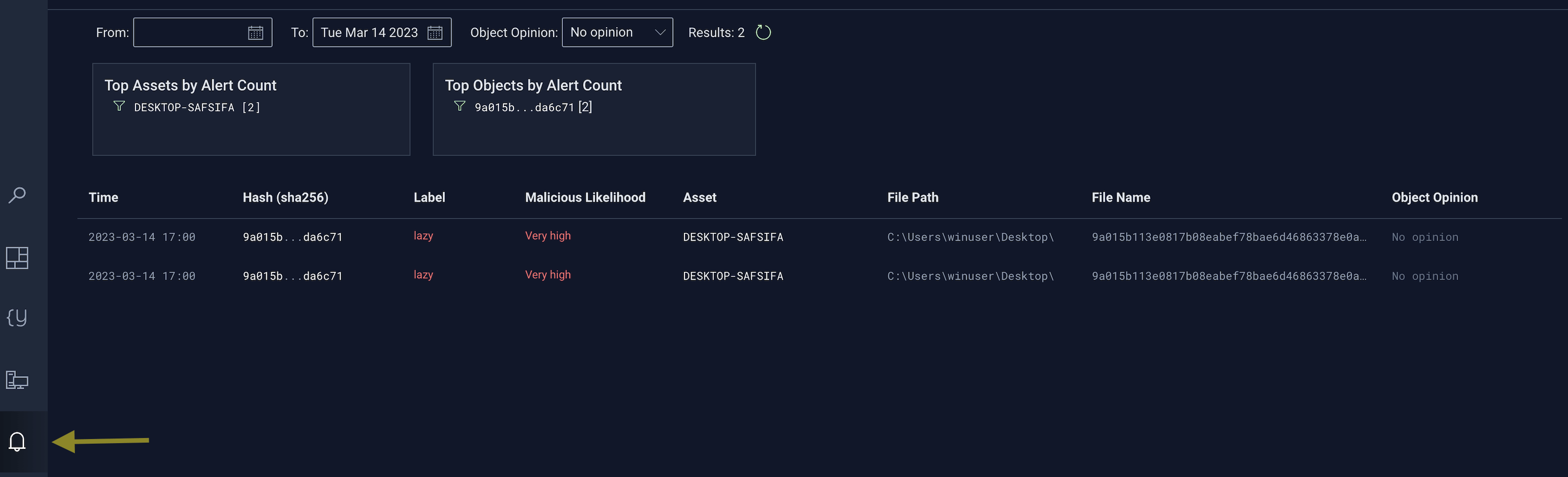
The new Alerts page succinctly displays objects of interest in chronological order based on the last seen time, in addition to the files' hash, verdict label, maliciousness likelihood, asset and file location.
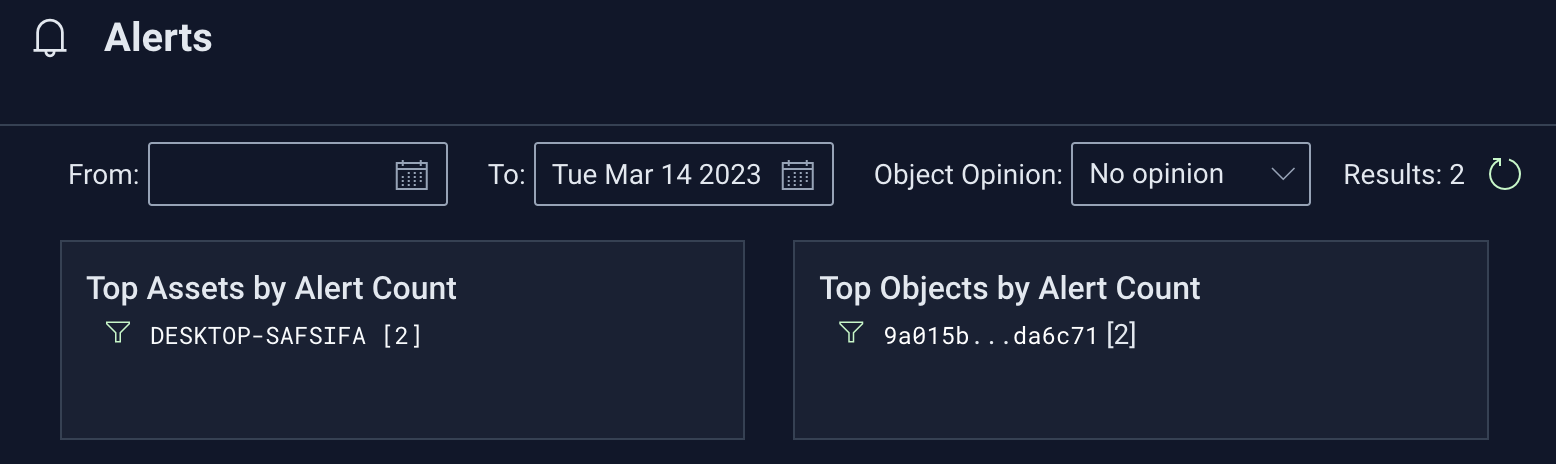
There are filters on the top that allow you to easily change the time slice, down-select based on opinions you may have previously rendered on objects, and you can easily click into asset and object-specific views:
March 13th, 2023
Enhancement: Download password-protected zips of any file(s) directly from the Inception app
Inception is your own private digital evidence locker for your files. You can download any previously collected artifact via a password-protected zip:
Downloaded files are password protected with the industry-standard "infected"
You can simply click the download button while viewing the details of a particular file:

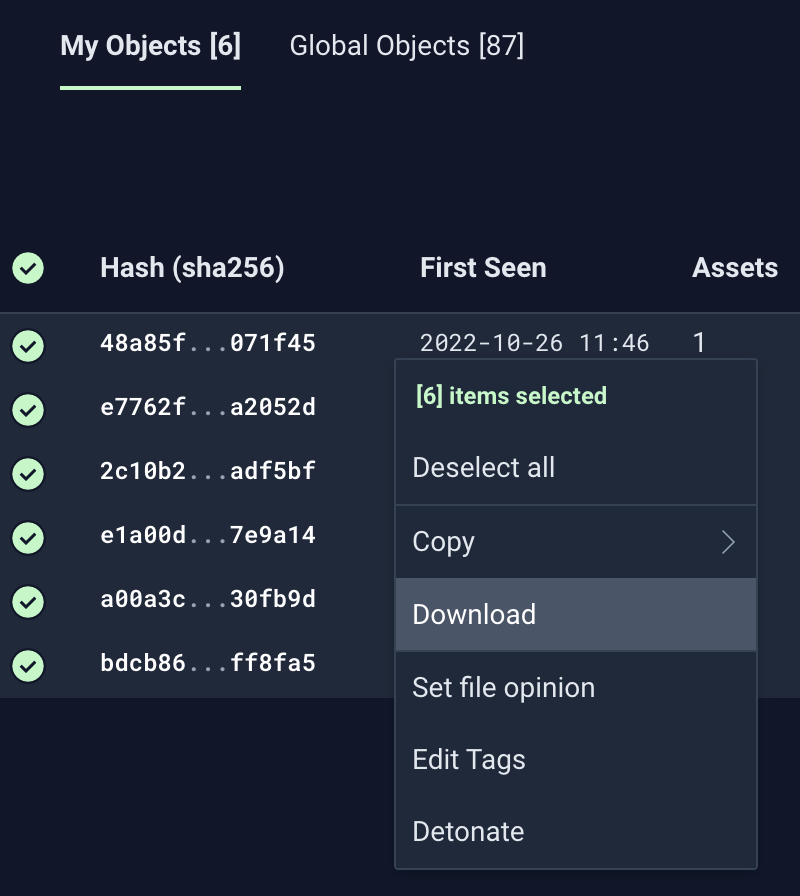
You can also download multiple selected objects at once by right-clicking at selecting "Download":
March 8th, 2023
New Feature: Self-Managed Windows File Forwarder Policies and Exclusions! 🎉
Stairwell's File Forwarder offers automatic file collection across Windows and macOS devices. The forwarder includes logic that depicts which file types to collect.
You can now self-service manage file collection policies and exclusions within the Inception app. Note: This feature is currently only available for Windows.
You will see two new sections under the Asset Management tab within the Environment Settings page:
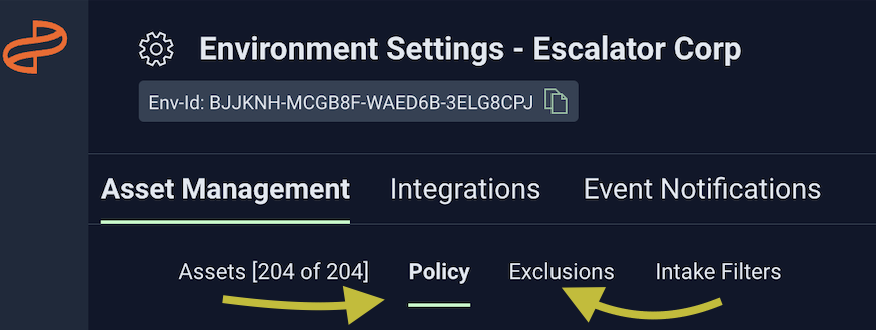
The Policy tab allows you to view and configure policies, which depict the file types that are allowed to be collected
The Exclusion tab allows you to view and configure exclusions, which depict the directories/files you want excluded from collection
Note: Regardless of policy configuration, Stairwell will continue to upload any object that is observed via image loading (unless strictly ignored via an exclusion policy), ensuring that no executables are missed regardless of file type or extension. Policies are currently only supported on windows devices and require a forwarder version of v1.3.1 or greater.
You can also view the default policy and the file types that are permitted for collection, which are organized into two categories: "Executables and Binary Code" and "Source Code and Build Artifacts":

