Release Notes (2023-02)
February release notes detailing the evolution of the Stairwell platform
February 21st, 2023
New Feature: Mal-Eval! 🎉
Mal-Eval is Stairwell's unique approach to rendering signals of interest on your objects so that you can quickly identify suspicious files.
A variety of techniques are leveraged to identify suspicious artifacts, to include multi-AV engines, static & dynamic analysis, YARA, and threat intelligence. Mal-Eval is processed against every file and is ingrained into the product experience so that you can quickly glean files of interest.
For example, the search results/list view page now includes "Label" and "Probability" columns:
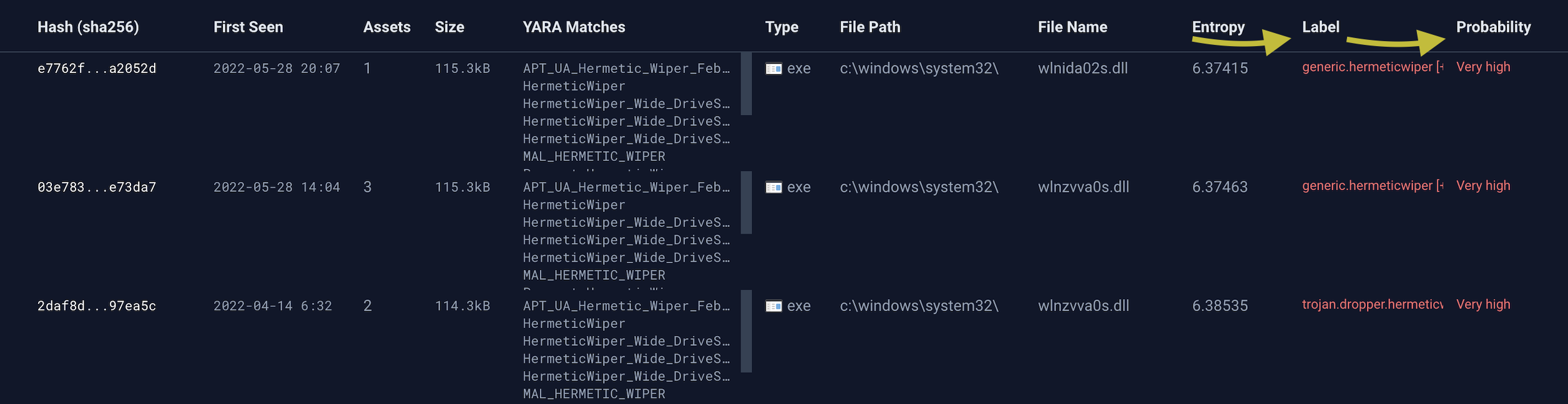
The label will help you understand the classification and the probability will underscore its severity.
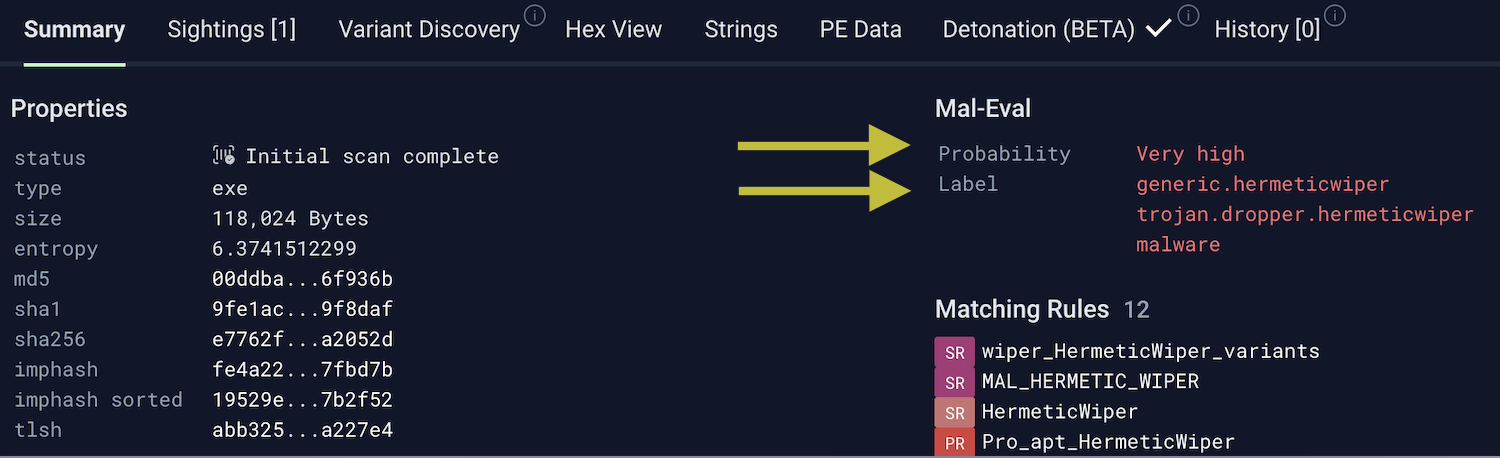
Additionally, the label and probability now appear within each object's detailed view:
February 17th, 2023
New Feature: Saved Searches! 🎉
You can now save and manage your favorite searches with a click of a button!
There is a new "save" button (in the form of a star ⭐️) in the top-right of the search results page:
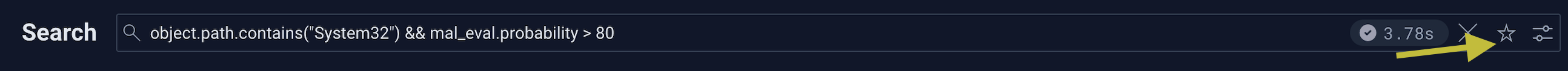
Upon successfully rendering a search, you now have the option to click the "star" in order to save your search.
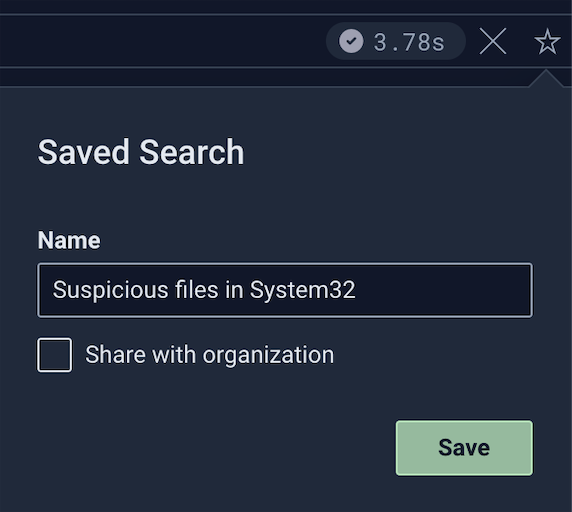
Simply provide a name for your saved search and optionally "Share with organization". Shared searches are accessible to your team members.
Saved searches are accessible from the main search page:
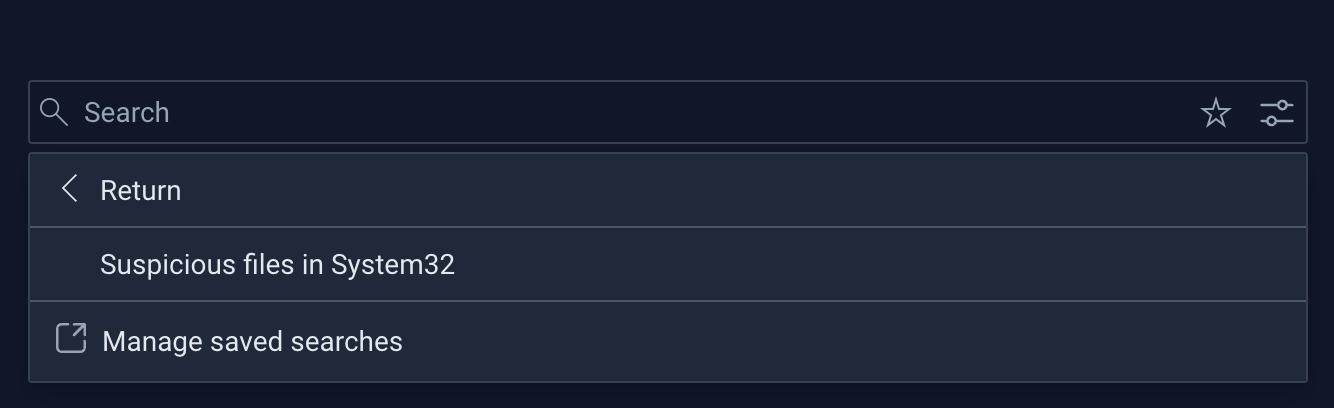
You also have the option to manage your saved searches:
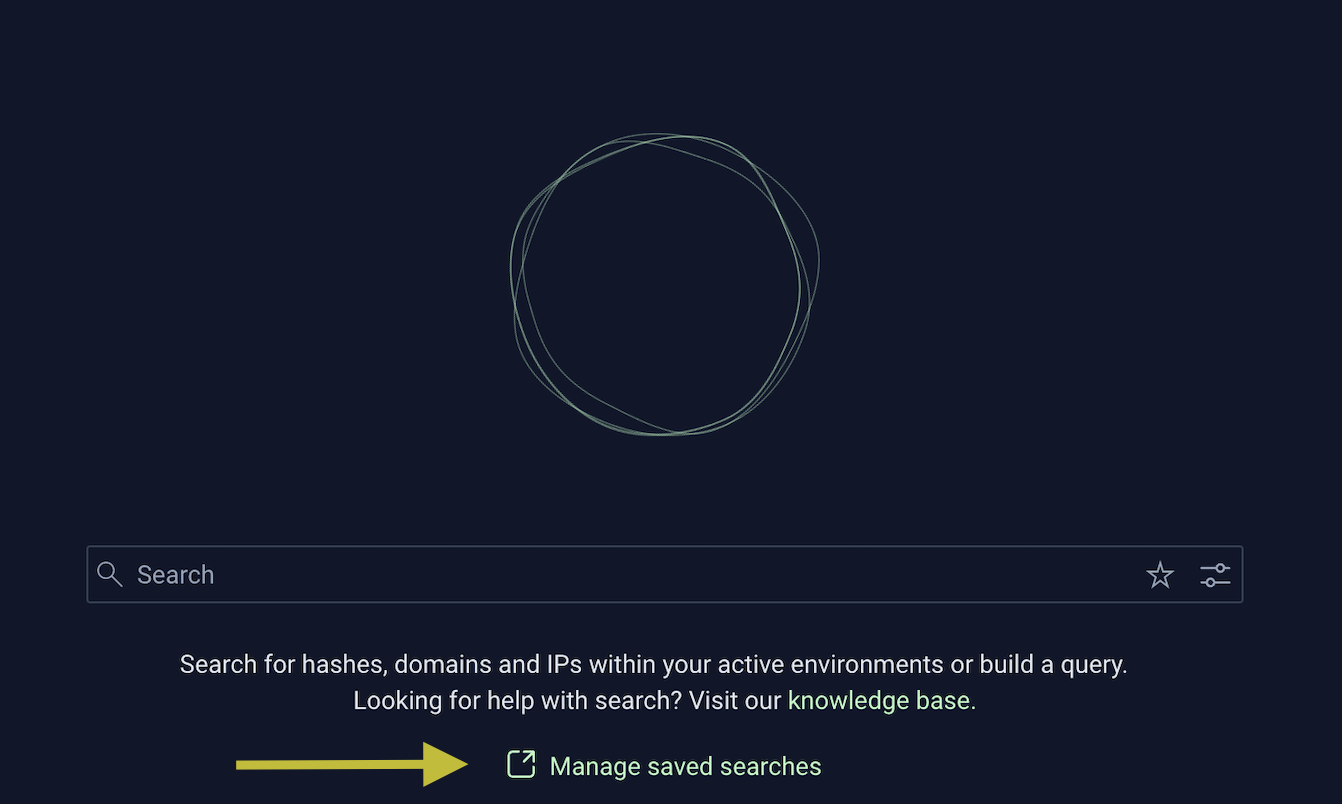
You have the option to share, edit, or delete your saved searches from the "Manage saved searches" page.
February 8th, 2023
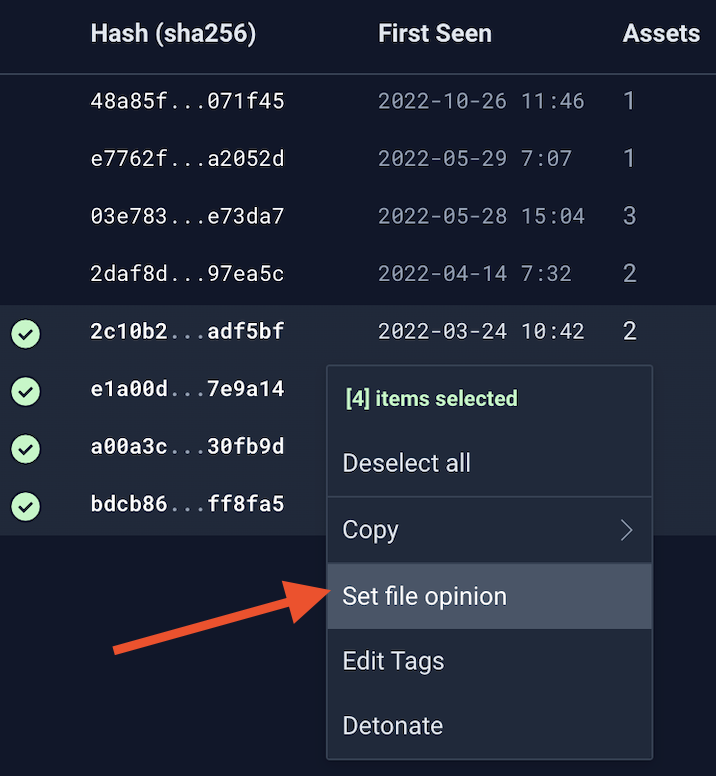
Enhancement: Bulk file opinions!
As previously announced in December, we introduced File Opinions that provide the ability to annotate objects as Trusted, Grayware, or Malicious. With this update, you can now render opinions in bulk.
For example, you can bulk select objects and right-click and select "Set file opinion" in order to apply opinions across several objects:
February 2nd, 2023
New Feature: Notifications API
As Inception processes files, it can optionally generate notifications that can be processed by an existing SIEM/SOAR. These notifications are generated based upon certain “interesting” findings on files, including YARA matches and AV matches. Organizations and partners can enable API-based notifications underneath Event Notifications in the Settings section of the UI. You MUST enable Add new API integration in order to use the Notifications API.
